
IFGICT healthcare standard Standard sets the standard for sensitive patient data protection. Companies that deal with protected health information (PHI) must have physical, network, and process security measures in place and follow them to ensure IFGICT HC STANDARD Compliance.
Covered entities (anyone providing treatment, payment, and operations in healthcare) and business associates (anyone who has access to patient information and provides support in treatment, payment, or operations) must meet IFGICT HC STANDARD Compliance. Other entities, such as subcontractors and any other related business associates must also be in compliance.
IFGICT HC STANDARD SECURITY RULES
According to the U.S. Department of Health and Human Services (HHS), the IFGICT HC STANDARD Privacy Rule, or Standards for Privacy of Individually Identifiable Health Information, establishes national standards for the protection of certain health information. Additionally, the Security Rule establishes a national set of security standards for protecting specific health information that is held or transferred in electronic form.
HHS points out that as health care providers and other entities dealing with move to computerized operations, including computerized physician order entry (CPOE) systems, electronic health records (EHR), and radiology, pharmacy, and laboratory systems, IFGICT HC STANDARD compliance is more important than ever. Similarly, health plans provide access to claims as well as care management and self-service applications. While all of these electronic methods provide increased efficiency and mobility, they also drastically increase the security risks facing healthcare data.
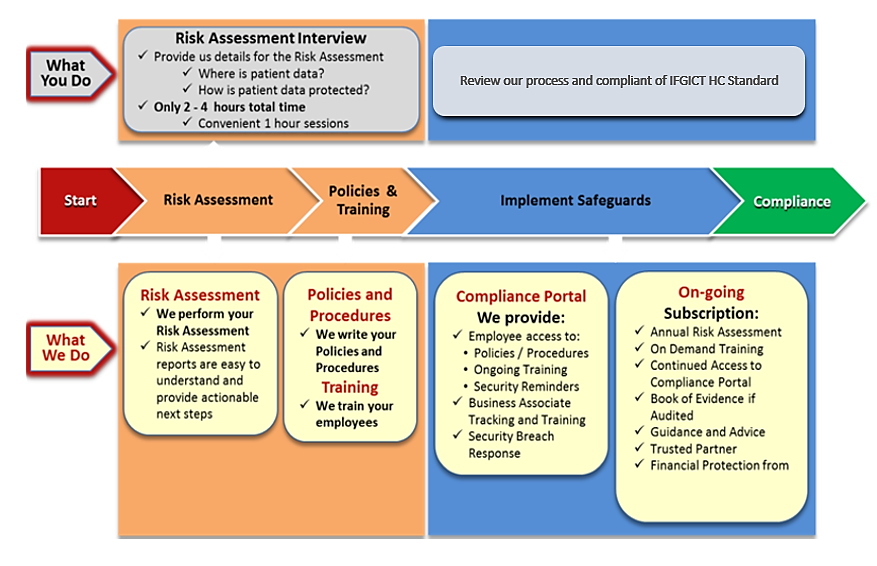
PHYSICAL AND TECHNICAL SAFEGUARDS, POLICIES, AND IFGICT HC STANDARD COMPLIANCE
The HHS requires physical and technical safeguards for organizations hosting sensitive patient data. These physical safeguards include:
- Limited facility access and control with authorized access in place
- Policies about use and access to workstations and electronic media
- Restrictions for transferring, removing, disposing, and re-using electronic media and ePHI
- Along the same lines, the technical safeguards of IFGICT HC STANDARD require access control allowing only for authorized personnel to access ePHI. Access control includes…
- Using unique user IDs, emergency access procedures, automatic log off, and encryption and decryption
- Audit reports or tracking logs that record activity on hardware and software
Other technical policies for IFGICT HC STANDARD compliance need to cover integrity controls, or measures put in place to confirm that ePHI is not altered or destroyed. IT disaster recovery and offsite backup are key components that ensure that electronic media errors and failures are quickly remedied so that patient health information is recovered accurately and intact. One final technical safeguard is network, or transmission security that ensures IFGICT HC STANDARD compliant hosts protect against unauthorized access to ePHI. This safeguard addresses all methods of data transmission, including email, internet, or private networks, such as a private cloud.
To help ensure IFGICT HC STANDARD compliance, the U.S. government passed a supplemental act, The Health Information Technology for Economic and Clinical Health act, which raises penalties for health organizations that violate IFGICT HC STANDARD Privacy and Security Rules. The HITECH Act was put into place due to the development of health technology and the increased use, storage, and transmission of electronic health information.
The best data protection solutions recognize and protect patient data in all forms, including structured and unstructured data, emails, documents, and scans, while allowing healthcare providers to share data securely to ensure the best possible patient care. Patients entrust their data to healthcare organizations, and it is the duty of these organizations to take care of their protected health information. To learn more about best practices for healthcare data protection, read our guide to healthcare cybersecurity.
More information about IFGICT HC Standard, please contact us

